Hi,
There’s finally some good news if you're trying to protect yourself from hackers. If you're looking for a hacker-proof password, simplicity may be the way to go. Here is a report on how you can build passwords that are impossible to hack, but easy to remember.
Enter password checker. Just type in www.microsoft.com/protect/yourself/password/checker.mspx or simply look it up on Google and click the link. Just type in a password, and you'll know instantly how strong or weak your option is.
Doing this will tell you how safe your password is from dictionary attacks that run through a whole dictionary or brute force attack that just runs through billions of combinations.
And for all you Mac OS users, password assistant is your designated guru.
We all know that a password is a random mix of numbers letters and symbols. blq4536/# is a great password but the problem is neither you or I can remember it. The solution is to come up with a random, logical combination.
There are four steps to making a great password.
The four step rules:
1. Just a dictionary single word, preferably in a different language. It is not at all powerful and easily broken but we're just getting started.
2. Now add a four digit number, a date of some significance that's not your date of birth.
3. Now end it with another word that relates to the website or page. That will do it.
4. But here's what will make it almost crack-proof. Add a symbol or two and then change the order.
Well that should care of your password needs. But what do you do if your office requires you to come up with a new one every 15 days? All I can say is good luck.
Tuesday, October 30, 2007
Sunday, October 14, 2007
Useful Alt+Tab Replacement Power Toy from Microsoft.
Hi All,
For those of you who use the Alt+Tab key combination to switch between open windows on your desktop, I am sure you have encountered times when you cannot distinguish one window from the other due to having more than one instance of the same program open.
Microsoft became aware of this draw-back after releasing the XP operating system and subsequently released a "Power Toy" to resolve this issue. The Power Toy resolves this issue by replacing the program icons with actual screen shots of your open windows. This way you can locate exactly which window you wish to switch to, which is immensely useful when navigating between several SAP windows at one time.
Here are pictures of using the Alt+Tab key combination both pre- and post- installation of the Power Toy:

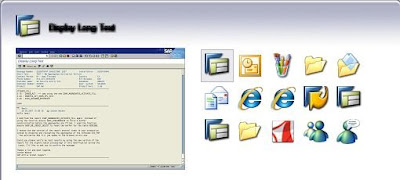
As you can see in the first example above, it is difficult to differentiate between the IE instances and the SAP instances by looking at the icons. In the subsequent example, the screen shot clearly differentiates the windows.
Here are the instructions to install this Microsoft power toy:
-Copy URL to browser:
http://download.Microsoft.com/download/whistler
/Install/2/WXP/EN-US/TaskswitchPowertoySetup.exe
-Choose "Run" from pop-up dialog box
-Choose "Run" a second time, this will kick-off the installation of the Power Toy
-Once you get the "Installation Complete" dialog, the toy is successfully installed. No need to reboot your PC.
For those of you who use the Alt+Tab key combination to switch between open windows on your desktop, I am sure you have encountered times when you cannot distinguish one window from the other due to having more than one instance of the same program open.
Microsoft became aware of this draw-back after releasing the XP operating system and subsequently released a "Power Toy" to resolve this issue. The Power Toy resolves this issue by replacing the program icons with actual screen shots of your open windows. This way you can locate exactly which window you wish to switch to, which is immensely useful when navigating between several SAP windows at one time.
Here are pictures of using the Alt+Tab key combination both pre- and post- installation of the Power Toy:


As you can see in the first example above, it is difficult to differentiate between the IE instances and the SAP instances by looking at the icons. In the subsequent example, the screen shot clearly differentiates the windows.
Here are the instructions to install this Microsoft power toy:
-Copy URL to browser:
http://download.Microsoft.com/download/whistler
/Install/2/WXP/EN-US/TaskswitchPowertoySetup.exe
-Choose "Run" from pop-up dialog box
-Choose "Run" a second time, this will kick-off the installation of the Power Toy
-Once you get the "Installation Complete" dialog, the toy is successfully installed. No need to reboot your PC.
Friday, September 21, 2007
Wednesday, September 19, 2007
Quality of Mobile
Would you like to know if your mobile is original or not ?????
Press the following on your mobile *#06# and the-international mobile equipment identity number appears. Then check the 7th and 8th numbers:
1 2 3 4 5 6 7 th 8 th 9 10 11 12 13 14 15
Phone serial no. x x x x x x ? ? x x x x x x x
IF the Seventh & Eighth digits are 02 or 20 this means your cell phone was assembled in Emirates which is very Bad quality
IF the Seventh & Eighth digits are 08 or 80 this means your cell phone was manufactured in Germany which is fair quality
IF the Seventh & Eighth digits are 01 or 10 this means your cell phone was manufactured in Finland which is very Good
IF the Seventh & Eighth digits are 00 this means your cell phone was manufactured in original factory which is the best Mobile Quality
IF the Seventh & Eighth digits are 13 this means your cell phone was assembled in Azerbaijan which is very Bad quality and also dangerous for your health
Press the following on your mobile *#06# and the-international mobile equipment identity number appears. Then check the 7th and 8th numbers:
1 2 3 4 5 6 7 th 8 th 9 10 11 12 13 14 15
Phone serial no. x x x x x x ? ? x x x x x x x
IF the Seventh & Eighth digits are 02 or 20 this means your cell phone was assembled in Emirates which is very Bad quality
IF the Seventh & Eighth digits are 08 or 80 this means your cell phone was manufactured in Germany which is fair quality
IF the Seventh & Eighth digits are 01 or 10 this means your cell phone was manufactured in Finland which is very Good
IF the Seventh & Eighth digits are 00 this means your cell phone was manufactured in original factory which is the best Mobile Quality
IF the Seventh & Eighth digits are 13 this means your cell phone was assembled in Azerbaijan which is very Bad quality and also dangerous for your health
Tuesday, September 18, 2007
For Abapers!!
Hi Friends,
For past so many days i haven't give any tips for the ABAPERS.
Here is the one good tip.
You dont have id to want to check something
inside SAP???
Hmmm.... it may sound impossible only if you are unaware of this:
Client 066 usually exists by default in any SAP System.
Log into the system using the client 066,
User : SAP*
Password : PASS
But hey, the system should be configured accordingly before you do this !.
(If that does not work out then you can always peep into your colleague's system!)Hahahaha!!
For past so many days i haven't give any tips for the ABAPERS.
Here is the one good tip.
You dont have id to want to check something
inside SAP???
Hmmm.... it may sound impossible only if you are unaware of this:
Client 066 usually exists by default in any SAP System.
Log into the system using the client 066,
User : SAP*
Password : PASS
But hey, the system should be configured accordingly before you do this !.
(If that does not work out then you can always peep into your colleague's system!)Hahahaha!!
Useful TIP to over come No subject mails in Outlook...
Forgot to mention subject, while writing an official mail and feel bad later???????
Yes…. It’s a concern for all…. A mail without a subject brings a bad impression on us.
To avoid this, Just follow the simple steps mentioned below and see the result.
Here below are the steps: -
1. Open your outlook
2. Press Alt+F11.
This opens the Visual Basic editor and then Press Ctrl+R which in turn open Project-Project 1 (left side)
3. On the Left Pane, one can see "Microsoft Outlook Objects" or "Project1", expand this.
Now one can see the "ThisOutLookSession".
4. Double click on "ThisOutLookSession". It will open up a code pane.
5. Copy and Paste the following code in the right pane.
(Code Pane) and save it
Private Sub Application_ItemSend(ByVal Item As Object, Cancel As Boolean)
Dim strSubject As String
strSubject = Item.Subject
If Len(Trim(strSubject)) = 0 Then
Prompt$ = "Subject is Empty. Are you sure you want to send the Mail?"
If MsgBox(Prompt$, vbYesNo + vbQuestion + vbMsgBoxSetForeground, "Check for Subject") = vbNo Then
Cancel = True End If End If End Sub
6. Now whenever u try to send a mail without subject, which will raise a pop-up to remind you
Yes…. It’s a concern for all…. A mail without a subject brings a bad impression on us.
To avoid this, Just follow the simple steps mentioned below and see the result.
Here below are the steps: -
1. Open your outlook
2. Press Alt+F11.
This opens the Visual Basic editor and then Press Ctrl+R which in turn open Project-Project 1 (left side)
3. On the Left Pane, one can see "Microsoft Outlook Objects" or "Project1", expand this.
Now one can see the "ThisOutLookSession".
4. Double click on "ThisOutLookSession". It will open up a code pane.
5. Copy and Paste the following code in the right pane.
(Code Pane) and save it
Private Sub Application_ItemSend(ByVal Item As Object, Cancel As Boolean)
Dim strSubject As String
strSubject = Item.Subject
If Len(Trim(strSubject)) = 0 Then
Prompt$ = "Subject is Empty. Are you sure you want to send the Mail?"
If MsgBox(Prompt$, vbYesNo + vbQuestion + vbMsgBoxSetForeground, "Check for Subject") = vbNo Then
Cancel = True End If End If End Sub
6. Now whenever u try to send a mail without subject, which will raise a pop-up to remind you
Wednesday, August 1, 2007
IDOC Technical Document
Intermediate Document
An IDoc is simply a data container that is used to exchange information between any two processes that can understand the syntax and semantics of the data. IDoc is not a process.
· IDocs are stored in the database.
· In the SAP system, IDocs are stored in database tables.
· IDocs are independent of the sending and receiving systems.
· IDocs are independent of the direction of data exchange.
Creation of IDOCs
Transaction code: WE 30
Defining Segment:
Creating Segment : Tcode – WE31
Creating Message Type : Tcode – we81
Assigning Message type to Idoc type: Tcode – we82
Process
The two processes for IDoc are Outbound Process and Inbound Process.
Outbound Process
When the data is sent out from the system, the process is called Outbound Process and the IDoc is known as Outbound IDoc.
Inbound Process
When the data is coming in, the process is called Inbound Process and the IDoc is known as Inbound IDoc.
Outbound Process (Sending System) Steps :
1) Goto Tcode SALE
 Click on Sending & Receiving Systems à Select Logical Systems
Click on Sending & Receiving Systems à Select Logical Systems
Here Define the Logical Systems à Click on Execute Button
Go for New Entries
1) System Name : LOG1
Description: Sending System
2) System Name : LOG2
Description: Receiving System
Press Enter & Save it will ask for Request if you want new request create new request or press continue for transferring the objects.
Assigning Client to the Logical System:
Select Assign Client to Logical Systems -> Execute

Ø 100 -> Double click on this and give the following information
Client : Sending System
City : Chennai
Logical System : LOG1
Currency :
Client role :
Ø 250 -> Double click on this and give the following information
Client : Receiving System
City :
Logical System : LOG2
Save this Data.
Step 2) For RFC Creation:
· Goto Tcode SM59 -> Select R/3 Connects
Click on create Button
 RFC Destination Name should be same as partner's logical system name and case sensitive to create the ports automatically while generating the partner profiles
RFC Destination Name should be same as partner's logical system name and case sensitive to create the ports automatically while generating the partner profiles
Give the information for required fields:
RFC Destination : LOG2
Connection type : 3
Target Host :
An IDoc is simply a data container that is used to exchange information between any two processes that can understand the syntax and semantics of the data. IDoc is not a process.
· IDocs are stored in the database.
· In the SAP system, IDocs are stored in database tables.
· IDocs are independent of the sending and receiving systems.
· IDocs are independent of the direction of data exchange.
Creation of IDOCs
Transaction code: WE 30
Defining Segment:
Creating Segment : Tcode – WE31
Creating Message Type : Tcode – we81
Assigning Message type to Idoc type: Tcode – we82
Process
The two processes for IDoc are Outbound Process and Inbound Process.
Outbound Process
When the data is sent out from the system, the process is called Outbound Process and the IDoc is known as Outbound IDoc.
Inbound Process
When the data is coming in, the process is called Inbound Process and the IDoc is known as Inbound IDoc.
Outbound Process (Sending System) Steps :
1) Goto Tcode SALE
 Click on Sending & Receiving Systems à Select Logical Systems
Click on Sending & Receiving Systems à Select Logical SystemsHere Define the Logical Systems à Click on Execute Button
Go for New Entries
1) System Name : LOG1
Description: Sending System
2) System Name : LOG2
Description: Receiving System
Press Enter & Save it will ask for Request if you want new request create new request or press continue for transferring the objects.
Assigning Client to the Logical System:
Select Assign Client to Logical Systems -> Execute

Ø 100 -> Double click on this and give the following information
Client : Sending System
City : Chennai
Logical System : LOG1
Currency :
Client role :
Ø 250 -> Double click on this and give the following information
Client : Receiving System
City :
Logical System : LOG2
Save this Data.
Step 2) For RFC Creation:
· Goto Tcode SM59 -> Select R/3 Connects
Click on create Button
 RFC Destination Name should be same as partner's logical system name and case sensitive to create the ports automatically while generating the partner profiles
RFC Destination Name should be same as partner's logical system name and case sensitive to create the ports automatically while generating the partner profilesGive the information for required fields:
RFC Destination : LOG2
Connection type : 3
Target Host :
System No : 00
Client :
User : Login user name
Password :
Save this & Test it and Remote Login

 Step 3) Goto Tcode BD64: – Click on the change button
Step 3) Goto Tcode BD64: – Click on the change button
Click on the create model view
Short Text: model view
Technical Name: LMOD
Save this & press ok
Select just created model view
Name: “LMOD”
Goto add message type
Model Name : LMOD
Sender : LOG1
Receiver : LOG2
Message type: ZAZHARMESS
 Save and press Enter.
Save and press Enter.
4) Goto Tcode BD82:
Give Model View : LMOD
Partner system : LOG2
Execute this by pressing F8
It will gives you sending system port No: A00000000089 (Like)

5) Goto Tcode BD64:
Select the model view
Goto à Edit à model view à Distribute
Press ok & Press Enter.
Run your Zprogram
REPORT ZAZHARIDOC1 .
DATA: Begin of imara occurs 0,
matnr like mara-matnr,
mtart like mara-mtart,
end of imara.
DATA: wamas_con LIKE edidc,
imas_data LIKE edidd OCCURS 0 WITH HEADER LINE,
icom_con LIKE edidc OCCURS 0 WITH HEADER LINE.
PARAMETERS: e_matnr LIKE mara-matnr,
e_msgtyp LIKE edidc-mestyp,
e_rcvprn LIKE edidc-rcvprn.
* retrive app. data from DB
SELECT matnr mtart FROM mara INTO TABLE imara WHERE
matnr = e_matnr.
*Master idoc control record
wamas_con-rcvprt = 'LS'.
wamas_con-rcvprn = e_rcvprn.
wamas_con-idoctp = 'ZAZHARIDOC'.
wamas_con-mestyp = e_msgtyp.
* master idoc data records
LOOP AT imara.
imas_data-segnam = 'ZAZHARSEG'.
move imara to imas_data-sdata .
APPEND imas_data.
ENDLOOP.
CALL FUNCTION 'MASTER_IDOC_DISTRIBUTE'
EXPORTING
master_idoc_control = wamas_con
TABLES
communication_idoc_control = icom_con
master_idoc_data = imas_data
COMMIT WORK.
6) Verifying Transfer of IDOCs Tcode – we05  ALE/IDOC Status Codes (outbound):
ALE/IDOC Status Codes (outbound):
01 IDoc Added
30 IDoc ready for dispatch
29 Error in ALE service Layer
12 Dispatch ok
Client :
User : Login user name
Password :
Save this & Test it and Remote Login

 Step 3) Goto Tcode BD64: – Click on the change button
Step 3) Goto Tcode BD64: – Click on the change buttonClick on the create model view
Short Text: model view
Technical Name: LMOD
Save this & press ok
Select just created model view
Name: “LMOD”
Goto add message type
Model Name : LMOD
Sender : LOG1
Receiver : LOG2
Message type: ZAZHARMESS
 Save and press Enter.
Save and press Enter.4) Goto Tcode BD82:
Give Model View : LMOD
Partner system : LOG2
Execute this by pressing F8
It will gives you sending system port No: A00000000089 (Like)

5) Goto Tcode BD64:
Select the model view
Goto à Edit à model view à Distribute
Press ok & Press Enter.
Run your Zprogram
REPORT ZAZHARIDOC1 .
DATA: Begin of imara occurs 0,
matnr like mara-matnr,
mtart like mara-mtart,
end of imara.
DATA: wamas_con LIKE edidc,
imas_data LIKE edidd OCCURS 0 WITH HEADER LINE,
icom_con LIKE edidc OCCURS 0 WITH HEADER LINE.
PARAMETERS: e_matnr LIKE mara-matnr,
e_msgtyp LIKE edidc-mestyp,
e_rcvprn LIKE edidc-rcvprn.
* retrive app. data from DB
SELECT matnr mtart FROM mara INTO TABLE imara WHERE
matnr = e_matnr.
*Master idoc control record
wamas_con-rcvprt = 'LS'.
wamas_con-rcvprn = e_rcvprn.
wamas_con-idoctp = 'ZAZHARIDOC'.
wamas_con-mestyp = e_msgtyp.
* master idoc data records
LOOP AT imara.
imas_data-segnam = 'ZAZHARSEG'.
move imara to imas_data-sdata .
APPEND imas_data.
ENDLOOP.
CALL FUNCTION 'MASTER_IDOC_DISTRIBUTE'
EXPORTING
master_idoc_control = wamas_con
TABLES
communication_idoc_control = icom_con
master_idoc_data = imas_data
COMMIT WORK.
6) Verifying Transfer of IDOCs Tcode – we05
 ALE/IDOC Status Codes (outbound):
ALE/IDOC Status Codes (outbound):01 IDoc Added
30 IDoc ready for dispatch
29 Error in ALE service Layer
12 Dispatch ok
03 Data passed to port ok.
Inbound Process (Receiving System) Steps:
Do the same step as you did in sending system
ü Creating IDoc
ü Defining the Segment
ü Creating Message Type
ü Assigning the Message Type
ü Defining the Logical System
ü Assigning the Logical System
ü Creating the Distribution Model
Goto Tcode – we57:
Assign function module to IDoc type
Module: Function module
Basic type:
Message type:
Direction: 2 (inbound)
Inbound Process (Receiving System) Steps:
Do the same step as you did in sending system
ü Creating IDoc
ü Defining the Segment
ü Creating Message Type
ü Assigning the Message Type
ü Defining the Logical System
ü Assigning the Logical System
ü Creating the Distribution Model
Goto Tcode – we57:
Assign function module to IDoc type
Module: Function module
Basic type:
Message type:
Direction: 2 (inbound)
Tuesday, July 10, 2007
Folder Lock without any S/W
Many people have been looking for an alternative way to lock folders without the use of any alternative software. So, here you go.
Open Notepad and copy the below code and save as locker.bat. Please don't forget to change your password in the code it's shown the place where to type your password. Now double click on locker .bat First time start, it will create folder with Locker automatically for u. After creation of the Locker folder, place the contents u want to lock inside the Locker Folder and run locker.bat again.
I hope this comes in handy.
**********************************************************
cls
@ECHO OFFtitle
Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End:UNLOCK
echo Enter password to Unlock folderset/p "pass=>"if NOT %pass%== type your password here goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" Locker
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
Open Notepad and copy the below code and save as locker.bat. Please don't forget to change your password in the code it's shown the place where to type your password. Now double click on locker .bat First time start, it will create folder with Locker automatically for u. After creation of the Locker folder, place the contents u want to lock inside the Locker Folder and run locker.bat again.
I hope this comes in handy.
**********************************************************
cls
@ECHO OFFtitle
Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End:UNLOCK
echo Enter password to Unlock folderset/p "pass=>"if NOT %pass%== type your password here goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" Locker
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
Monday, May 28, 2007
Keyboard Shortcuts for Windows users
CTRL+ TAB - Move forward through tabs.
CTRL+ SHIFT + TAB - Move backward through tabs.
TAB - Move forward through options.
SHIFT+ TAB - Move backward through options.
ALT+ Underlined letter - Carry out the corresponding command or select the corresponding option.
ENTER - Carry out the command for the active option or button.
SPACEBAR - Select or clear the check box if the active option is a check box.
Arrow keys - Select a button if the active option is a group of option buttons.
F1 - Display help.
F4 - Display the items in the active list.
BACKSPACE - Open a folder one level up if a folder is selected in the Save As or Open dialogbox.
CTRL + C - Copy
CTRL+ X - Cut
CTRL+ V - Paste
CTRL+ Z - Undo
DELETE - DeleteSHIFT+ DELETE - Delete selected item permanently without placing the item in the Recycle Bin
CTRL while dragging an item - Copy selected item.
CTRL+ SHIFT while dragging an item - Create shortcut to selected item.
F2 - Rename selected item.
CTRL+ RIGHT ARROW - Move the insertion point to the beginning of the next word.
CTRL+ LEFT ARROW - Move the insertion point to the beginning of the previous word.
CTRL+ DOWN ARROW - Move the insertion point to the beginning of the next paragraph.
CTRL+ UP ARROW - Move the insertion point to the beginning of the previous paragraph.
CTRL+ SHIFT with any of the arrow keys - Highlight a block of text.
SHIFT with any of the arrow keys - Select more than one item in a window or on the desktop, or select text within a document.
CTRL+ A - Select all.
F3 - Search for a file or folder.
ALT+ ENTER - View properties for the selected item.
ALT+F4 - Close the active item, or quit the active program.
ALT+ Enter - Displays the properties of the selected object.
ALT+ SPACEBAR - Opens the shortcut menu for the active window.
CTRL+F4 - close the active document in programs that allow you to have multiple documents open simultaneously.
ALT+ TAB - Switch between open items.
ALT+ ESC - Cycle through items in the order they were opened.
F6 - Cycle through screen elements in a window or on the desktop.
F4 - Display the Address bar list in My Computer or Windows Explorer.
SHIFT+F10 - Display the shortcut menu for the selected item.
ALT+ SPACEBAR - Display the System menu for the active window.
CTRL+ ESC - Display the Start menu.
ALT+ Underlined letter in a menu name - Display the corresponding menu Underlined letter in a command name on an open menu - Carry out the corresponding demand.
F10 - Activate the menu bar in the active program.
RIGHT ARROW - Open the next menu to the right, or open a submenu.
LEFT ARROW - Open the next menu to the left, or close a submenu.
F5 - Refresh the active window.
BACKSPACE - View the folder one level up in My computer or Windows Explorer.
ESC - Cancel the current task.
SHIFT when you insert a CD into the CD-Rom drive - Prevent the CD from automatically playing.
Windows Key - Display or hide the Start menu.
Windows Key+ BREAK - Display the System Properties dialog box.
Windows Key+ D - Show the desktop.
Windows Key+ M - Minimize all windows.
Windows Key+ Shift+ M - Restores minimized windows.
Windows Key+ E - Open My Computer.
Windows Key+ F - Search for a file or folder.
CTRL+ Windows Key+ F - Search for computers.
Windows Key+F1 - Display Windows Help.
Windows Key+ L - Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain.
Windows Key+ R - Open the Run dialog box.
Windows Key+ U - Open Utility Manager.
CTRL+ SHIFT + TAB - Move backward through tabs.
TAB - Move forward through options.
SHIFT+ TAB - Move backward through options.
ALT+ Underlined letter - Carry out the corresponding command or select the corresponding option.
ENTER - Carry out the command for the active option or button.
SPACEBAR - Select or clear the check box if the active option is a check box.
Arrow keys - Select a button if the active option is a group of option buttons.
F1 - Display help.
F4 - Display the items in the active list.
BACKSPACE - Open a folder one level up if a folder is selected in the Save As or Open dialogbox.
CTRL + C - Copy
CTRL+ X - Cut
CTRL+ V - Paste
CTRL+ Z - Undo
DELETE - DeleteSHIFT+ DELETE - Delete selected item permanently without placing the item in the Recycle Bin
CTRL while dragging an item - Copy selected item.
CTRL+ SHIFT while dragging an item - Create shortcut to selected item.
F2 - Rename selected item.
CTRL+ RIGHT ARROW - Move the insertion point to the beginning of the next word.
CTRL+ LEFT ARROW - Move the insertion point to the beginning of the previous word.
CTRL+ DOWN ARROW - Move the insertion point to the beginning of the next paragraph.
CTRL+ UP ARROW - Move the insertion point to the beginning of the previous paragraph.
CTRL+ SHIFT with any of the arrow keys - Highlight a block of text.
SHIFT with any of the arrow keys - Select more than one item in a window or on the desktop, or select text within a document.
CTRL+ A - Select all.
F3 - Search for a file or folder.
ALT+ ENTER - View properties for the selected item.
ALT+F4 - Close the active item, or quit the active program.
ALT+ Enter - Displays the properties of the selected object.
ALT+ SPACEBAR - Opens the shortcut menu for the active window.
CTRL+F4 - close the active document in programs that allow you to have multiple documents open simultaneously.
ALT+ TAB - Switch between open items.
ALT+ ESC - Cycle through items in the order they were opened.
F6 - Cycle through screen elements in a window or on the desktop.
F4 - Display the Address bar list in My Computer or Windows Explorer.
SHIFT+F10 - Display the shortcut menu for the selected item.
ALT+ SPACEBAR - Display the System menu for the active window.
CTRL+ ESC - Display the Start menu.
ALT+ Underlined letter in a menu name - Display the corresponding menu Underlined letter in a command name on an open menu - Carry out the corresponding demand.
F10 - Activate the menu bar in the active program.
RIGHT ARROW - Open the next menu to the right, or open a submenu.
LEFT ARROW - Open the next menu to the left, or close a submenu.
F5 - Refresh the active window.
BACKSPACE - View the folder one level up in My computer or Windows Explorer.
ESC - Cancel the current task.
SHIFT when you insert a CD into the CD-Rom drive - Prevent the CD from automatically playing.
Windows Key - Display or hide the Start menu.
Windows Key+ BREAK - Display the System Properties dialog box.
Windows Key+ D - Show the desktop.
Windows Key+ M - Minimize all windows.
Windows Key+ Shift+ M - Restores minimized windows.
Windows Key+ E - Open My Computer.
Windows Key+ F - Search for a file or folder.
CTRL+ Windows Key+ F - Search for computers.
Windows Key+F1 - Display Windows Help.
Windows Key+ L - Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain.
Windows Key+ R - Open the Run dialog box.
Windows Key+ U - Open Utility Manager.
Search Engines
THE WEB GOES LIVE FOR BUSINESS
In the early days of the Internet, Yahoo’s directory service was the way we surfed the web because it was still indexable and classifiable by human editors. But the web grew too fast for this to last. The first-generation of search engines such as Altavista, Lycos, Webcrawler and Excite mirrored the pages on the web and provided textual search capabilities on the documents. It was good for a short while, until spammers figured out how to infiltrate the system. For a while, it seemed we would need to go back to maintaining bookmarks and remembering URLs to go to different sites. And then along come Google with its PageRank technology, which enabled search based on the importance of pages as measured by incoming links. Search was back in vogue—and has stayed that way ever since.
Much of the web that we see around us is the Reference Web. The content is mostly static. Pretty much anything digital will be accessible at our fingertips, if it is not already so. It is like being in a large digital library. Millions of websites have aggregated all kinds of information and made it available for anyone, mostly for free. More than a decade of enhancements in publishing technology has also made it simple for users to add to the treasure trove that’s already out there.
In the early days of the Internet, Yahoo’s directory service was the way we surfed the web because it was still indexable and classifiable by human editors. But the web grew too fast for this to last. The first-generation of search engines such as Altavista, Lycos, Webcrawler and Excite mirrored the pages on the web and provided textual search capabilities on the documents. It was good for a short while, until spammers figured out how to infiltrate the system. For a while, it seemed we would need to go back to maintaining bookmarks and remembering URLs to go to different sites. And then along come Google with its PageRank technology, which enabled search based on the importance of pages as measured by incoming links. Search was back in vogue—and has stayed that way ever since.
Much of the web that we see around us is the Reference Web. The content is mostly static. Pretty much anything digital will be accessible at our fingertips, if it is not already so. It is like being in a large digital library. Millions of websites have aggregated all kinds of information and made it available for anyone, mostly for free. More than a decade of enhancements in publishing technology has also made it simple for users to add to the treasure trove that’s already out there.
THE SEARCH FOR GOOGLE'S SECRETS :
THE SEARCH FOR GOOGLE'S SECRETS :
I was leading to a briefing session at the world's most talked-about company briefly lost its way enroute. It led to the inevitable wisecrack once we reached – while the world searches on Google, there we were searching for Google! But the end of the journey presented a true reward. We entered the vibrant campus just as a shareholders' briefing session was on - which had given the whole place the look of a college campus on graduation day rather than the birthplace of one of Silicon Valley's proudest entrepreneurial start-ups! What makes Google such a great company – the darling of the stock market, the top pick of all the business schools ahead of long-term favourites like McKinsey, and even the hedge funds? A place where even the hardened "seen it all" types are delighted to be invited for a free lunch? The free lunch is certainly a draw – at a canteen, which offers a choice of 14 cuisines! There is also a health club with more treadmills and cardio equipment than you would see in the biggest gyms. These too are among the keys to building an exciting new culture around the "Googler" community and making Google itself an aspirational employer.
But it does not stop at that as the briefing team amply demonstrated with its breadth of social and economic knowledge coupled with the able-to-deploy technology to satisfy every stated and even some latent needs of the planet's web community As co. founder Larry Page said last week, the goal of the company is to produce a search engine that understands what you want before you key it in. No wonder then that Google's share of the search market grew to a staggering 65 percent in the US in the month of April and no wonder, too, that CEO Eric Schmidt commenting on the buzz around the potential Microsoft-Yahoo merger, said, "It would change the competitive dynamic but it would not cause us to do anything different."
The writer is Deputy chairman & MD of Zensar Technologies and vice-chairman of Nasscom
I was leading to a briefing session at the world's most talked-about company briefly lost its way enroute. It led to the inevitable wisecrack once we reached – while the world searches on Google, there we were searching for Google! But the end of the journey presented a true reward. We entered the vibrant campus just as a shareholders' briefing session was on - which had given the whole place the look of a college campus on graduation day rather than the birthplace of one of Silicon Valley's proudest entrepreneurial start-ups! What makes Google such a great company – the darling of the stock market, the top pick of all the business schools ahead of long-term favourites like McKinsey, and even the hedge funds? A place where even the hardened "seen it all" types are delighted to be invited for a free lunch? The free lunch is certainly a draw – at a canteen, which offers a choice of 14 cuisines! There is also a health club with more treadmills and cardio equipment than you would see in the biggest gyms. These too are among the keys to building an exciting new culture around the "Googler" community and making Google itself an aspirational employer.
But it does not stop at that as the briefing team amply demonstrated with its breadth of social and economic knowledge coupled with the able-to-deploy technology to satisfy every stated and even some latent needs of the planet's web community As co. founder Larry Page said last week, the goal of the company is to produce a search engine that understands what you want before you key it in. No wonder then that Google's share of the search market grew to a staggering 65 percent in the US in the month of April and no wonder, too, that CEO Eric Schmidt commenting on the buzz around the potential Microsoft-Yahoo merger, said, "It would change the competitive dynamic but it would not cause us to do anything different."
The writer is Deputy chairman & MD of Zensar Technologies and vice-chairman of Nasscom
Create a Button to Reboot Windows Xp
Create a Button to reboot ur windows Xp:
To create a reboot icon on your desktop: Right click on an open area of the desktop Select New/Shortcut Enter in"shutdown -r -t 00" - no quotes Press Next For the name, enter Reboot or anything you like.Click Finish.
To create a reboot icon on your desktop: Right click on an open area of the desktop Select New/Shortcut Enter in"shutdown -r -t 00" - no quotes Press Next For the name, enter Reboot or anything you like.Click Finish.
Signatures & Personality
Signatures & Personality
The various types of Signatures you come across & the attitude of a person are listed below:
# SINGLE UNDERLINE BELOW THE SIGN!!
These persons are very confident and are good personalities. They are a little bit selfish but believe in "Happiness of human life"
# TWO DOTS BELOW THE SIGN!!
These persons are considered to be Romantic, can easily change their fiancées as if they change their clothes. They prefer beauty in other persons & they themselves try to look beautiful. They easily attract others.
# SINGLE DOT BELOW THE SIGN!
These persons are more inclined towards classical arts, simple & are very cool. If you loose faith with them, then these persons will never look back at you. Hence its always better to be careful with these people.
# NO UNDERLINES OR DOTS BELOW THE SIGN!!
These persons enjoy their life in their own way, never pay attention to others views. These are considered to be good natured but are selfish too.
# RANDOM SIGN, NO SIMILARITY BETWEEN NAME & SIGN!!
These persons try to be very smart, hide each & every matter, never say anything in straight forward manner, never pay attention to the other person of what he is talking of.
# RANDOM SIGN, SIMILARITY BETWEEN NAME & SIGN!!
These persons are considered to be intelligent but never think. These people change their ideas & views as fast as the wind changes its direction of flow. They never think whether that particular thing is right or wrong.You can win them just by flattering them.
# SIGN IN PRINTED LETTERS!!
These persons are very kind to us, have a good heart, selfless, are ready to sacrifice their life for the sake of their near & dear. But these seem to think a lot and may get angry very soon.
# WRITING COMPLETE NAME AS THEIR SIGN!!
These persons are very kind hearted, can adjust themselves to any environment & to the person they are talking. These persons are very firm on their views & posses a lot of will power.
The various types of Signatures you come across & the attitude of a person are listed below:
# SINGLE UNDERLINE BELOW THE SIGN!!
These persons are very confident and are good personalities. They are a little bit selfish but believe in "Happiness of human life"
# TWO DOTS BELOW THE SIGN!!
These persons are considered to be Romantic, can easily change their fiancées as if they change their clothes. They prefer beauty in other persons & they themselves try to look beautiful. They easily attract others.
# SINGLE DOT BELOW THE SIGN!
These persons are more inclined towards classical arts, simple & are very cool. If you loose faith with them, then these persons will never look back at you. Hence its always better to be careful with these people.
# NO UNDERLINES OR DOTS BELOW THE SIGN!!
These persons enjoy their life in their own way, never pay attention to others views. These are considered to be good natured but are selfish too.
# RANDOM SIGN, NO SIMILARITY BETWEEN NAME & SIGN!!
These persons try to be very smart, hide each & every matter, never say anything in straight forward manner, never pay attention to the other person of what he is talking of.
# RANDOM SIGN, SIMILARITY BETWEEN NAME & SIGN!!
These persons are considered to be intelligent but never think. These people change their ideas & views as fast as the wind changes its direction of flow. They never think whether that particular thing is right or wrong.You can win them just by flattering them.
# SIGN IN PRINTED LETTERS!!
These persons are very kind to us, have a good heart, selfless, are ready to sacrifice their life for the sake of their near & dear. But these seem to think a lot and may get angry very soon.
# WRITING COMPLETE NAME AS THEIR SIGN!!
These persons are very kind hearted, can adjust themselves to any environment & to the person they are talking. These persons are very firm on their views & posses a lot of will power.
Thursday, May 17, 2007
Shocking Messages Telegrams
TELEGRAM #1
A daughter sends a telegram to her father on her clearing B.Ed exams, which the father receives as :
TELEGRAM #2
A husband, while he is on a business trip to a hill station sends a telegram to his wife : "I wish you were here." The message received by wife:
"I wish you were her."
TELEGRAM #3
A wife with near maturing pregnancy goes to railway station to return to her husband. At the reservation counter , while her turn came, it was the last ticket. Taking pity on a very old lady next to her in the queue, she offered her berth to the old lady and sent a telegram to her husband which reached as:
"Shall be coming tomorrow, heavy rush in the train, gave birth to an old lady."
Message This is really a cool one :
A man wants to celebrate his wife's Birthday by throwing a party . So he goes to order a birthday cake. The salesman asks him what message he wants to put on the cake.Well he thinks for a while and says: let's put, "you are not getting older you are getting better". The salesman asks "how do you want me to put it?" The man says, Well put "You are not getting older", at the top and"You are getting better" at the bottom. The real fun didn't start until the cake was opened the entire party watched the message decorated on the cake:
"You are not getting older at the top,
You are getting better at the bottom".
TELEGRAM #5
A man from Agra went to Ajmer . His wife was in her parent's house in Delhi . When the man went to Ajmer , he asked his servant to send a telegram to his wife indicating about his trip to Ajmer . He sent a telegram. When the wife received the telegram, she fainted. It was written:
'sethji aaj mar gaye ! ( Sethji Ajmer gaye ).
A daughter sends a telegram to her father on her clearing B.Ed exams, which the father receives as :
"Father, your daughter has been successful in BED."
TELEGRAM #2
A husband, while he is on a business trip to a hill station sends a telegram to his wife : "I wish you were here." The message received by wife:
"I wish you were her."
TELEGRAM #3
A wife with near maturing pregnancy goes to railway station to return to her husband. At the reservation counter , while her turn came, it was the last ticket. Taking pity on a very old lady next to her in the queue, she offered her berth to the old lady and sent a telegram to her husband which reached as:
"Shall be coming tomorrow, heavy rush in the train, gave birth to an old lady."
Message This is really a cool one :
A man wants to celebrate his wife's Birthday by throwing a party . So he goes to order a birthday cake. The salesman asks him what message he wants to put on the cake.Well he thinks for a while and says: let's put, "you are not getting older you are getting better". The salesman asks "how do you want me to put it?" The man says, Well put "You are not getting older", at the top and"You are getting better" at the bottom. The real fun didn't start until the cake was opened the entire party watched the message decorated on the cake:
"You are not getting older at the top,
You are getting better at the bottom".
TELEGRAM #5
A man from Agra went to Ajmer . His wife was in her parent's house in Delhi . When the man went to Ajmer , he asked his servant to send a telegram to his wife indicating about his trip to Ajmer . He sent a telegram. When the wife received the telegram, she fainted. It was written:
'sethji aaj mar gaye ! ( Sethji Ajmer gaye ).
Wednesday, May 9, 2007
World Tallest Man
 Robert Pershing Wadlow
Robert Pershing WadlowRobert Pershing Wadlow (1918 - 1940) was and is the tallest human being ever recorded. He reached 8' 11.1" (272 cm) in height and 490 pounds (222.26 kg) in weight before his death at the age of 22. His height was due to an overactive pituitary gland.
Robert Wadlow was born in Alton, Illinois on February 22 1918. At the time he weighed only 8' 6 ounces (3.8 kg). He attracted attention due to his rapid growth when all his four siblings grew at a more normal speed. At the age of 13 he became the world's tallest Boy Scout with a height of 7'4 (224 cm). At age 18 his height was 8'4 (254 cm) and he weighed 390 pounds (177 kg). His size 37 shoes cost $100.00 a pair.At the age of 20 Wadlow signed a contract with the International Shoe Company; he received free shoes in exchange for a promotional tour. He traveled all around the USA with his father.
In 1936 he enrolled in Shurtleff College with the intention of studying law.By 1937 he had exceeded the previous records. However, his size begun to take its toll. He had to keep braces in his feet to walk and had little sensation in them.
On July 4 1940 Wadlow was taken ill in Manistee, Michigan; a faulty brace had caused a blister and bad infection. Doctors treated him with blood transfusions and emergency surgery but his fever got worse. On July 15 1940 he died in his sleep. He was buried in Alton on July 19.
Tuesday, May 8, 2007
Jokes Entertainment - Osama Bin-Laden
When will I Die?
Osama Bin-Laden stared believing in astrology and went to a special astrologist to ask him when will be the day he dies.
"You wil die on an American holiday", said the astrologist.
"How can you be so sure of that?" asked Bin-Laden.
"Well, any day you die will be an American holiday".
Osama Bin-Laden stared believing in astrology and went to a special astrologist to ask him when will be the day he dies.
"You wil die on an American holiday", said the astrologist.
"How can you be so sure of that?" asked Bin-Laden.
"Well, any day you die will be an American holiday".
Monday, May 7, 2007
Monday, April 23, 2007
Suprising Bug in Windows
For those of you using Windows:
1.) Open an empty notepad file
2.) Type "Bush hid the facts" (without the quotes)
3.) Save it as whatever you want.
4.) Close it, and re-open it.
Watch Star War Movie in ur Command Prompt
Watch Star War Movie in ur Command Prompt
Type this in your command prompt or through run command
telnet towel.blinkenlights.nl
And See the Star War Movies in your command Prompt.
Type this in your command prompt or through run command
telnet towel.blinkenlights.nl
And See the Star War Movies in your command Prompt.
Hidden Music in WINDOWS XP
HIDDEN MUSIC IN WINDOWS xp!!!
Try it.
1->Set the folder option to show all hidden and system files
2->Go to C:\WINDOWS\system32\oobe\images
3->Find a file by name title.wma and play it
Try it.
1->Set the folder option to show all hidden and system files
2->Go to C:\WINDOWS\system32\oobe\images
3->Find a file by name title.wma and play it
Fun & Entertainment
Todays Dinner:
Sardarji standing below a tube light with a open mouth……………..WHY? because his doctor advised him“Todays dinner shouldbe light
Horses and Sardars:
There were two sardars, Zail Singh & Jarnail Singh.Both of them bought a horse each. “How will we know which is your & which is mine?” asked Zail. ”Easy” repliedJarnail. “I’ll cut mine’s tail,yours will be the one with tail” This was heard by a few boys ,they cut the other’s tail too.Next morning the confusion continued. “Don’t worry “retorted Jarnail.“I’ll tie a bell around its neck; yours will be the one without the bell.” The boys heard this also & cut the bell. The next day, Zail got frustrated & said “Okay now the last criterion, white will be yours & black will be mine
Sardarji standing below a tube light with a open mouth……………..WHY? because his doctor advised him“Todays dinner shouldbe light
Horses and Sardars:
There were two sardars, Zail Singh & Jarnail Singh.Both of them bought a horse each. “How will we know which is your & which is mine?” asked Zail. ”Easy” repliedJarnail. “I’ll cut mine’s tail,yours will be the one with tail” This was heard by a few boys ,they cut the other’s tail too.Next morning the confusion continued. “Don’t worry “retorted Jarnail.“I’ll tie a bell around its neck; yours will be the one without the bell.” The boys heard this also & cut the bell. The next day, Zail got frustrated & said “Okay now the last criterion, white will be yours & black will be mine
The Story behind Orkut
A guy lost his girlfriend in a train accident.... but the gal's name nowhere appeared in the dead list. This guy grew up n became IT technical architect in his late 20?s, achievement in itself!!.
He hired developers from the whole globe and plan to make a software where he could search for his gf through the web..
Things went as planned... and he found her, after losing millions of dollars and 3 long years!! It was time to shut down the search operation, when the CEO of Google had a word with this guy and took over this application,This Software made a whopping 1 billion dollars profit in its first year, which we today know as ORKUT .
The guy's name is ORKUT BUYUKKOTEN . Yes its named after him only. Today he is paid a hefty sum by Google for the things we do like scrapping. He is expected to b the richest person by 2009. ORKUT BUYUKKOTEN today has 13 assistants to monitor his scrapbook & 8 to
monitor his friends-list. He gets around 20,000 friend-requests a day &about 85,000 scraps!!!Some other Cool Facts abt this guy:
* He gets $12 from Google when every person registers to this website.
* He also gets $10 when you add somebody as a friend.
* He gets $8 when your friend's friend adds you as a friend & gets $6 if anybody adds you as friend in the resulting chain.
* He gets $5 when you scrap somebody & $4 when somebody scraps you.
* He also gets $200 for each photograph you upload on Orkut.
* He gets $2.5 when you add your friend in the crush-list or in the hot-list.
* He gets $2 when you become somebody's fan.
* He gets $1.5 when somebody else becomes your fan.
* He even gets $1 every time you logout of Orkut.
* He gets $0.5 every time you just change your profile-photograph.
* He also gets $0.5 every time you read your friend's scrap-book & $0.5 every time
you view your friend's friend-list.
He hired developers from the whole globe and plan to make a software where he could search for his gf through the web..
Things went as planned... and he found her, after losing millions of dollars and 3 long years!! It was time to shut down the search operation, when the CEO of Google had a word with this guy and took over this application,This Software made a whopping 1 billion dollars profit in its first year, which we today know as ORKUT .
The guy's name is ORKUT BUYUKKOTEN . Yes its named after him only. Today he is paid a hefty sum by Google for the things we do like scrapping. He is expected to b the richest person by 2009. ORKUT BUYUKKOTEN today has 13 assistants to monitor his scrapbook & 8 to
monitor his friends-list. He gets around 20,000 friend-requests a day &about 85,000 scraps!!!Some other Cool Facts abt this guy:
* He gets $12 from Google when every person registers to this website.
* He also gets $10 when you add somebody as a friend.
* He gets $8 when your friend's friend adds you as a friend & gets $6 if anybody adds you as friend in the resulting chain.
* He gets $5 when you scrap somebody & $4 when somebody scraps you.
* He also gets $200 for each photograph you upload on Orkut.
* He gets $2.5 when you add your friend in the crush-list or in the hot-list.
* He gets $2 when you become somebody's fan.
* He gets $1.5 when somebody else becomes your fan.
* He even gets $1 every time you logout of Orkut.
* He gets $0.5 every time you just change your profile-photograph.
* He also gets $0.5 every time you read your friend's scrap-book & $0.5 every time
you view your friend's friend-list.
Technology that retrieves sounds in the wall
Technology that retrieves sounds in the wall :
Scientists have developed a technology that can retrieve sounds and conversations that get recorded in the walls around us. An Indian scientist and a software engineer have been working on the secret project for 17 years costing more than 255 crore rupees. Their identities are kept secret for security reasons. "Well, the methodology is in great demand by the Americans and in Europe it's worth billions of dollars," the scientist said. "We have had kidnap threats, so we can only go public when our security is guaranteed".
How does it works:
Every wall in a room is made up of millions and millions of atoms. Each atom is a collection of electrons, protons and neutrons - all electrically charged and constantly moving. When anyone inside the four walls of a room speaks, the sound carries energy that travels in waves and hits the walls. When this voice energy hits the atoms in a wall the electrons and protons are disturbed. Each word spoken hits the atoms with a different energy level and disturbs the atoms differently. Scientists have worked on the software and technology that can measure how each atom has been disturbed and match each unique disturbance with a unique word. The technology virtually "replays" the sequence of words that have been spoken inside the walls. It's like rewinding a tape recorder and you can go as far back in history as you want.
Historic secrets:
The scientists have already recorded many historic conversations some of which are classified as secret. They have extracted a few words by Aurangzeb from the walls of the Red Fort in Delhi and from the walls of the Agra Fort. They contain what Shahjahan said to Noorjahan on the night before she died. It's not just voices from the distant past that can be replayed - when you leave your room at work your boss can tap the walls and hear all that you said.The amazing technology could change the way we live. Inside the bedroom or boardroom - nothing is a secret any more. It will change way nations spy on each other and it will most certainly lead to the re-writing of history books. The technology will be available commercially for sale 12 months from now in April 2008
Scientists have developed a technology that can retrieve sounds and conversations that get recorded in the walls around us. An Indian scientist and a software engineer have been working on the secret project for 17 years costing more than 255 crore rupees. Their identities are kept secret for security reasons. "Well, the methodology is in great demand by the Americans and in Europe it's worth billions of dollars," the scientist said. "We have had kidnap threats, so we can only go public when our security is guaranteed".
How does it works:
Every wall in a room is made up of millions and millions of atoms. Each atom is a collection of electrons, protons and neutrons - all electrically charged and constantly moving. When anyone inside the four walls of a room speaks, the sound carries energy that travels in waves and hits the walls. When this voice energy hits the atoms in a wall the electrons and protons are disturbed. Each word spoken hits the atoms with a different energy level and disturbs the atoms differently. Scientists have worked on the software and technology that can measure how each atom has been disturbed and match each unique disturbance with a unique word. The technology virtually "replays" the sequence of words that have been spoken inside the walls. It's like rewinding a tape recorder and you can go as far back in history as you want.
Historic secrets:
The scientists have already recorded many historic conversations some of which are classified as secret. They have extracted a few words by Aurangzeb from the walls of the Red Fort in Delhi and from the walls of the Agra Fort. They contain what Shahjahan said to Noorjahan on the night before she died. It's not just voices from the distant past that can be replayed - when you leave your room at work your boss can tap the walls and hear all that you said.The amazing technology could change the way we live. Inside the bedroom or boardroom - nothing is a secret any more. It will change way nations spy on each other and it will most certainly lead to the re-writing of history books. The technology will be available commercially for sale 12 months from now in April 2008
Thursday, April 19, 2007
For ABAPers Difference between LSMW and BDC
What is the exact difference between BDC and LSMW?
BDC is the way to transfer data by writing a batch input program which can use either session or call transaction method.
LSMW used to transfer data without/less code.
What type of data we transfer using LSMW?
LSMW is best suited for transferring master data.
Actually BDC and LSMW are not comparable at all.
for example LSMW itself can use BDC as a way of mass data transfer.
BDC is a mass data transfer technique via screen logic of existing SAP Data entry transactions. It behaves as if you are manually making thousand of entires into sap system as a background job. And that is probably the reason why BAPI's are preffered over BDC's.
On the other hand LSMW is a tool to facilitate DATA migration from other legacy systems ... It contains step by step procedure for data migration.
Like Managing Data Migration Projects , Creating Source Structures , Mapping Source structures wid Target structures , etc etc
LSMW internally might well be using the following techniqes for data transfer..1. IDOX2. Direct Input / BDC4. BAPI's
LSMW is an encapsulated data transfer tool. It can provide the same functionality as BDC infact much more but when coming to techinical perspective most the parameters are encapulated. To listout some of the differences :
LSMW is basicaly designed for a fuctional consultant who do not do much coding but need to explore the fuctionality while BDC is designed for a technical consultant.
LSMW offers different techinque for migrating data: Direct input ,BAPI,Idoc,Batch input recording. While bdc basically uses recording.
LSMW mapping is done by SAP while in BDC we have to do it explicitly .
LSMW is basically for standard SAP application while bdc basically for customized application.
Coding can be done flexibly in BDC when compared to LSMW
Diff. between BDC and LSMW."The Data Transfer Workbench (or DX Workbench, transaction SXDA) is an integrated SAP tool that supports data transfer and analysis. It does not have the built-in features for mapping for source structures to target structures, but it will allow you to integrate Legacy System Migration Workbench (LSMW) objects as processing tasks within a run definition. The DX workbench has many features for creating test data and performing data migrations - for example, logging of data migration runs. However, if you need to map or convert data, you should use the LSMW. Or, you can integrate your LSMW objects as task within a more user-friendly data migration run, in which the LSMW project steps "Read data", "Convert data," and "Start IDoc processing" are automated and use the features of both tools. If you donot need logging and automated data migration runs, you can perform your data migration without the DX Workbench."
釘atch Data Communication (BDC) is the oldest batch interfacing technique that SAP provided since the early versions of R/3. BDC is not a typical integration tool, in the sense that, it can be only be used for uploading data into R/3 and so it is not bi-directional. BDC works on the principle of simulating user input for transactional screen, via an ABAP program. Typically the input comes in the form of a flat file. The ABAP program reads this file and formats the input data screen by screen into an internal table (BDCDATA). The transaction is then started using this internal table as the input and executed in the background.
In 舛all Transaction・ the transactions are triggered at the time of processing itself and so the ABAP program must do the error handling. It can also be used for real-time interfaces and custom error handling & logging features. Whereas in Batch Input Sessions, the ABAP program creates a session with all the transactional data, and this session can be viewed, scheduled and processed (using Transaction SM35) at a later time. The latter technique has a built-in error processing mechanism too.
Batch Input (BI) programs still use the classical BDC approach but doesn稚 require an ABAP program to be written to format the BDCDATA. The user has to format the data using predefined structures and store it in a flat file. The BI program then reads this and invokes the transaction mentioned in the header record of the file.
Direct Input (DI) programs work exactly similar to BI programs. But the only difference is, instead of processing screens they validate fields and directly load the data into tables using standard function modules. For this reason, DI programs are much faster (RMDATIND - Material Master DI program works at least 5 times faster) than the BDC counterpart and so ideally suited for loading large volume data. DI programs are not available for all application areas.
BDC is the way to transfer data by writing a batch input program which can use either session or call transaction method.
LSMW used to transfer data without/less code.
What type of data we transfer using LSMW?
LSMW is best suited for transferring master data.
Actually BDC and LSMW are not comparable at all.
for example LSMW itself can use BDC as a way of mass data transfer.
BDC is a mass data transfer technique via screen logic of existing SAP Data entry transactions. It behaves as if you are manually making thousand of entires into sap system as a background job. And that is probably the reason why BAPI's are preffered over BDC's.
On the other hand LSMW is a tool to facilitate DATA migration from other legacy systems ... It contains step by step procedure for data migration.
Like Managing Data Migration Projects , Creating Source Structures , Mapping Source structures wid Target structures , etc etc
LSMW internally might well be using the following techniqes for data transfer..1. IDOX2. Direct Input / BDC4. BAPI's
LSMW is an encapsulated data transfer tool. It can provide the same functionality as BDC infact much more but when coming to techinical perspective most the parameters are encapulated. To listout some of the differences :
LSMW is basicaly designed for a fuctional consultant who do not do much coding but need to explore the fuctionality while BDC is designed for a technical consultant.
LSMW offers different techinque for migrating data: Direct input ,BAPI,Idoc,Batch input recording. While bdc basically uses recording.
LSMW mapping is done by SAP while in BDC we have to do it explicitly .
LSMW is basically for standard SAP application while bdc basically for customized application.
Coding can be done flexibly in BDC when compared to LSMW
Diff. between BDC and LSMW."The Data Transfer Workbench (or DX Workbench, transaction SXDA) is an integrated SAP tool that supports data transfer and analysis. It does not have the built-in features for mapping for source structures to target structures, but it will allow you to integrate Legacy System Migration Workbench (LSMW) objects as processing tasks within a run definition. The DX workbench has many features for creating test data and performing data migrations - for example, logging of data migration runs. However, if you need to map or convert data, you should use the LSMW. Or, you can integrate your LSMW objects as task within a more user-friendly data migration run, in which the LSMW project steps "Read data", "Convert data," and "Start IDoc processing" are automated and use the features of both tools. If you donot need logging and automated data migration runs, you can perform your data migration without the DX Workbench."
釘atch Data Communication (BDC) is the oldest batch interfacing technique that SAP provided since the early versions of R/3. BDC is not a typical integration tool, in the sense that, it can be only be used for uploading data into R/3 and so it is not bi-directional. BDC works on the principle of simulating user input for transactional screen, via an ABAP program. Typically the input comes in the form of a flat file. The ABAP program reads this file and formats the input data screen by screen into an internal table (BDCDATA). The transaction is then started using this internal table as the input and executed in the background.
In 舛all Transaction・ the transactions are triggered at the time of processing itself and so the ABAP program must do the error handling. It can also be used for real-time interfaces and custom error handling & logging features. Whereas in Batch Input Sessions, the ABAP program creates a session with all the transactional data, and this session can be viewed, scheduled and processed (using Transaction SM35) at a later time. The latter technique has a built-in error processing mechanism too.
Batch Input (BI) programs still use the classical BDC approach but doesn稚 require an ABAP program to be written to format the BDCDATA. The user has to format the data using predefined structures and store it in a flat file. The BI program then reads this and invokes the transaction mentioned in the header record of the file.
Direct Input (DI) programs work exactly similar to BI programs. But the only difference is, instead of processing screens they validate fields and directly load the data into tables using standard function modules. For this reason, DI programs are much faster (RMDATIND - Material Master DI program works at least 5 times faster) than the BDC counterpart and so ideally suited for loading large volume data. DI programs are not available for all application areas.
How to create a ALV grid
report z_alv_data_display .
data : begin of itab occurs 100,
belnr like bsas-belnr,
budat like bsas-budat,
dmbtr like bsas-dmbtr,
xblnr like bsas-xblnr,
end of itab.
data i_repid like sy-repid.
data i_lines like sy-tabix.
type-pools: slis.
data: int_fcat type slis_t_fieldcat_alv,
is_layout type slis_fieldcat_alv.
data: wa_fieldcat like line of int_fcat.
selection-screen: begin of block b1.
parameters : ddate like bsas-bldat,
glact like bsas-hkont.
selection-screen:end of block b1.
start-of-selection.
select bldat dmbtr belnr budat hkont xblnr from bsas
into (itab-bldat, itab-dmbtr, itab-belnr, itab-budat, itab-hkont, itab-xblnr) where bldat eq ddate and hkont eq glact.
append itab.
endselect.
select bldat dmbtr belnr budat hkont xblnr from bsis
into (itab-bldat, itab-dmbtr, itab-belnr, itab-budat, itab-hkont, itab-xblnr) where bldat eq ddate and hkont eq glact.
append itab.
endselect.
end-of-selection.
i_repid = sy-repid.
is_layout-col_pos = 1.
is_layout-fieldname = 'BELNR'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Document No'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 2.
is_layout-fieldname = 'BLDAT'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Document Dt'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 3.
is_layout-fieldname = 'BUDAT'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Posting Dt'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 4.
is_layout-fieldname = 'HKONT'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'GL Act No'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 5.
is_layout-fieldname = 'DMBTR'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Amt(Lcl Curncy)'.
append is_layout to int_fcat. clear is_layout.
is_layout-col_pos = 6.
is_layout-fieldname = 'XBLNR'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Reference'.
append is_layout to int_fcat.
clear is_layout.
*----------------------------------------------------------
* Call for ALV list display
call function 'REUSE_ALV_LIST_DISPLAY'
exporting
I_CALLBACK_PROGRAM = 'Z_ALV_SIMPLE_EXAMPLE_WITH_ITAB' i_callback_program = i_repid
it_fieldcat = int_fcat[]
i_save = 'A' tables
t_outtab = itab[]
exceptions program_error = 1
others = 2. if sy-subrc <> 0.
write: / 'Returncode', sy-subrc,
'from FUNCTION REUSE_ALV_LIST_DISPLAY'.
endif.
data : begin of itab occurs 100,
belnr like bsas-belnr,
budat like bsas-budat,
dmbtr like bsas-dmbtr,
xblnr like bsas-xblnr,
end of itab.
data i_repid like sy-repid.
data i_lines like sy-tabix.
type-pools: slis.
data: int_fcat type slis_t_fieldcat_alv,
is_layout type slis_fieldcat_alv.
data: wa_fieldcat like line of int_fcat.
selection-screen: begin of block b1.
parameters : ddate like bsas-bldat,
glact like bsas-hkont.
selection-screen:end of block b1.
start-of-selection.
select bldat dmbtr belnr budat hkont xblnr from bsas
into (itab-bldat, itab-dmbtr, itab-belnr, itab-budat, itab-hkont, itab-xblnr) where bldat eq ddate and hkont eq glact.
append itab.
endselect.
select bldat dmbtr belnr budat hkont xblnr from bsis
into (itab-bldat, itab-dmbtr, itab-belnr, itab-budat, itab-hkont, itab-xblnr) where bldat eq ddate and hkont eq glact.
append itab.
endselect.
end-of-selection.
i_repid = sy-repid.
is_layout-col_pos = 1.
is_layout-fieldname = 'BELNR'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Document No'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 2.
is_layout-fieldname = 'BLDAT'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Document Dt'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 3.
is_layout-fieldname = 'BUDAT'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Posting Dt'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 4.
is_layout-fieldname = 'HKONT'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'GL Act No'.
append is_layout to int_fcat.
clear is_layout.
is_layout-col_pos = 5.
is_layout-fieldname = 'DMBTR'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Amt(Lcl Curncy)'.
append is_layout to int_fcat. clear is_layout.
is_layout-col_pos = 6.
is_layout-fieldname = 'XBLNR'.
is_layout-tabname = 'ITAB'.
is_layout-seltext_l = 'Reference'.
append is_layout to int_fcat.
clear is_layout.
*----------------------------------------------------------
* Call for ALV list display
call function 'REUSE_ALV_LIST_DISPLAY'
exporting
I_CALLBACK_PROGRAM = 'Z_ALV_SIMPLE_EXAMPLE_WITH_ITAB' i_callback_program = i_repid
it_fieldcat = int_fcat[]
i_save = 'A' tables
t_outtab = itab[]
exceptions program_error = 1
others = 2. if sy-subrc <> 0.
write: / 'Returncode', sy-subrc,
'from FUNCTION REUSE_ALV_LIST_DISPLAY'.
endif.
Tuesday, April 10, 2007
Virus Information
Top Viruses:
1. TROJ_GENERIC
Malware Type: Trojan This is the Trend Micro generic detection for low-threat Trojans. It also installs itself as a browser helper object (BHO) by creating certain registry keys.
2. ADW_CNSMIN.G
Malware Type: Adware This adware arrives on a system via the Internet, or bundled with other applications. It does not have a valid End-User License Agreement (EULA).It is a plugin that can monitor or manipulate a user's Internet activity by adding itself in the Layered Service Provider (LSP). Like most adware, it generates pop-up avertisements.
3. WORM_NYXEM.E
Malware Type: Worm This worm propagates by attaching copies of itself to email messages that it sends to target addresses, using its own SMTP engine. Through this SMTP engine, it is able to easily send the email message without using other mailing applications, such as Microsoft Outlook.
4. WORM_ANIG.A
Malware Type: Worm This memory-resident worm propagates by dropping copies of itself in shared network drives. It steals login information and saves the obtained data in a file, which can be retrieved by a remote user. Its keylogger component substitutes the standard Microsoft Graphical Identification and Authentication DLL (MSGINA.DLL) to carry out its information-stealing routine.
5. POSSIBLE_INFOSTL
Malware Type: Susupicious files This is the Trend Micro detection for suspicious files that manifest behavior and characteristics similar to known variants of the following spyware:TSPY_LEGMIR TSPY_LINEAGE TSPY_QQPASS
6. HTML_NETSKY.P
Malware Type: HTML This HTML malware arrives as an email with an executable file attachment that is detected by Trend Micro as WORM_NETSKY.P. It exploits a known vulnerability in Internet Explorer versions 5.01 and 5.5 known as the Automatic Execution of Embedded MIME Type. This vulnerability causes Internet Explorer to automatically run executable file attachments in email messages.
7. WORM_NETSKY.DAM
Malware Type: WormThis is Trend Micro's detection for the damaged samples of WORM_NETSKY variants. It runs on Windows 95, 98, ME, NT, 2000 and XP.
8. TROJ_HORST.HFMalware Type: TrojanThis Trojan usually arrives as a file dropped by other malware or as a file downloaded unknowingly by a user when visiting malicious Web sites.
1. TROJ_GENERIC
Malware Type: Trojan This is the Trend Micro generic detection for low-threat Trojans. It also installs itself as a browser helper object (BHO) by creating certain registry keys.
2. ADW_CNSMIN.G
Malware Type: Adware This adware arrives on a system via the Internet, or bundled with other applications. It does not have a valid End-User License Agreement (EULA).It is a plugin that can monitor or manipulate a user's Internet activity by adding itself in the Layered Service Provider (LSP). Like most adware, it generates pop-up avertisements.
3. WORM_NYXEM.E
Malware Type: Worm This worm propagates by attaching copies of itself to email messages that it sends to target addresses, using its own SMTP engine. Through this SMTP engine, it is able to easily send the email message without using other mailing applications, such as Microsoft Outlook.
4. WORM_ANIG.A
Malware Type: Worm This memory-resident worm propagates by dropping copies of itself in shared network drives. It steals login information and saves the obtained data in a file, which can be retrieved by a remote user. Its keylogger component substitutes the standard Microsoft Graphical Identification and Authentication DLL (MSGINA.DLL) to carry out its information-stealing routine.
5. POSSIBLE_INFOSTL
Malware Type: Susupicious files This is the Trend Micro detection for suspicious files that manifest behavior and characteristics similar to known variants of the following spyware:TSPY_LEGMIR TSPY_LINEAGE TSPY_QQPASS
6. HTML_NETSKY.P
Malware Type: HTML This HTML malware arrives as an email with an executable file attachment that is detected by Trend Micro as WORM_NETSKY.P. It exploits a known vulnerability in Internet Explorer versions 5.01 and 5.5 known as the Automatic Execution of Embedded MIME Type. This vulnerability causes Internet Explorer to automatically run executable file attachments in email messages.
7. WORM_NETSKY.DAM
Malware Type: WormThis is Trend Micro's detection for the damaged samples of WORM_NETSKY variants. It runs on Windows 95, 98, ME, NT, 2000 and XP.
8. TROJ_HORST.HFMalware Type: TrojanThis Trojan usually arrives as a file dropped by other malware or as a file downloaded unknowingly by a user when visiting malicious Web sites.
Portable Hard Drives
A Portable hard drive is one of the best available solutions in contemporary times for storing high volumes of data and keeping it secure. In a Floppy disk there is no guarantee of data retention and the amount of data stored is negligible, as compared to a portable storage device. The portable storage device is considered to be a better option than a CD (700 MB) or a DVD (4 GB or 8 in case of a dual layer DVD), as one does not need a writer to copy data on it. These drives are a viable option compared to thumb drives/pen drives. A thumb drive can store up to 2 GB of data, which is much less compared to the portable drives. Also, carrying a portable drive is not a problem at all, given its sleek and compact design. The potential of a portable drive to store high quantity (20, 40, 60, 80, 120 GB) of data is also an advantage.The portable storage drives available in the market today are plug and play devices. One does not need anything else to run it. Just plug the device to a PC/notebook via a USB cable and you are on. The devices are USB 1.0 and 2.0 compatible. It is also very easy to copy files from a PC/notebook to a portable storage device. Just copy the files from the former and paste it in the device. You can also keep the device attached to the PC and run files from it. Some of the popular brand portable storage devices available in the market include LaCie, Iomega, Fujitsu, and SeaGate among others.
Wednesday, April 4, 2007
Hard-Drive Encryption
Hard-drive encryption is a technology that encrypts the data stored on a hard drive using sophisticated mathematical functions. Data on an encrypted hard drive cannot be read by anyone who does not have access to the appropriate key or password. This can help prevent access to data by unauthorized persons and provides a layer of security against hackers and other online threats.
The concept of hard-drive encryption is simple enough. When a file is written to the drive, it is automatically encrypted by specialized software. When a file is read from the drive, the software automatically decrypts it while leaving all other data on the drive encrypted. The encryption and decryption processes are transparent to all common applications such as word processors, databases, spreadsheets or imaging programs. A computer equipped with hard-drive encryption appears, from the user's point of view, to function as any other computer would.
Windows Vista Enterprise and Ultimate editions offer a hard-drive encryption program called BitLocker that employs two-factor authentication.
The concept of hard-drive encryption is simple enough. When a file is written to the drive, it is automatically encrypted by specialized software. When a file is read from the drive, the software automatically decrypts it while leaving all other data on the drive encrypted. The encryption and decryption processes are transparent to all common applications such as word processors, databases, spreadsheets or imaging programs. A computer equipped with hard-drive encryption appears, from the user's point of view, to function as any other computer would.
Windows Vista Enterprise and Ultimate editions offer a hard-drive encryption program called BitLocker that employs two-factor authentication.
Friday, March 30, 2007
Yahoo unlimited storage

Yahoo Mail Announces Unlimited Storage
"Yahoo is announcing that all Yahoo Mail users will have unlimited storage starting in May 2007. The current storage limit is 1 GB per account (2 GB for $20/year premium users). With this change, Yahoo leapfrogs Gmail (2.8 GB and growing) and Live.com Mail (2GB)."
Azhar -- Nokia NSeries
At Consumer Electronic Show taking place in Las Vegas Nokia has come up with a number of offerings, specifically updates to two Nseries-branded models and an all-round new tablet for web surfing. Running a few steps forward, I feel obliged to say that this very announcement has more of a predictable rather than revolutionary move in it, but first things first.
Nokia N76. Eventually, Nokia just could not resist and joined the race where the top prize is “slimmest phone ever” – at a glance its new model utilizes many curves and shapes of the this market’s icon - Motorola RAZR, but as you might have already guessed, its pluses are lying in a slightly different field, since the N76 is in fact a smartphone running Symbian OS augmented with S60 3rd edition FP1. Speaking about why we suppose the RAZR was on the head designer’s table at the time when he was sketching out Nokia N76 – a metal keypad is here, along with dents at the bottom and other bits and pieces giving away its origin.
As a matter of fact, the company has managed to squeeze the hardware of the N76 into a casing only 13.7 mm deep, not due to cutting-edge alterations to the chassis; basically they have made it taller. Generally speaking Nokia 6290 is an exact replica of Nokia N76 – there aren’t many differences to dwell upon. While the 6290 measures 94x50x20.8 mm, the N76 presents us with 106.5x52x13.7 mm, meaning that it is a tad wider, almost 1 cm taller and all this for being reasonably thin.
Since we have started comparing these two handsets, then another place where the N76 falls short of Nokia 6290 is battery life. Nokia N76 utilizes a 700 mAh battery (BL-4B); as the manufacturer claims it can keep the phone up and running for up to 200 hours in standby mode and provides about 2 hours 45 minutes of talk time. A curious fact – for Nokia 6290 carrying a 950 mAh BL-5F onboard, the maker says 240 hours of lifetime in standby mode is its utmost limit. Keeping in mind that it would be a hastiness to take for granted what manufacturer claims regarding battery life, let us try to look into the real battery life put up by Nokia N76, or, better to say, how much worse it will be. Examining capacity of two batteries point-blank, then the gap will make up 35 percent, at that in normal conditions on average load Nokia 6290 manages to keep itself alive for about 2 days. Taking account of nonlinearity of charge wearing out, we can rightfully state that Nokia N76 is a handset that will require you to plug in the charge every evening, of course, if you are actually going to use it.
Software-wise these two models are wholly identical, the only difference is possibility to go into landscape mode on the internal display. Support for A2DP profile is currently missing.
Apart from the battery life and absence of stereo-speakers, Nokia 6290 and Nokia N76 are twins. I should mention it that the design of the senior solution is different and one could hardly make a mistake about that – Nokia N76 is positioned as a fashion solution, with vivid trims speaking in favor of this assumption, specifically red and black color schemes. Overall the handset looks pretty stylish and will surely appeal to many; to me this is what the company is betting on – to draw attention of those who have struck Nokia 6290 off their short-lists for some reasons.
Nokia N76. Eventually, Nokia just could not resist and joined the race where the top prize is “slimmest phone ever” – at a glance its new model utilizes many curves and shapes of the this market’s icon - Motorola RAZR, but as you might have already guessed, its pluses are lying in a slightly different field, since the N76 is in fact a smartphone running Symbian OS augmented with S60 3rd edition FP1. Speaking about why we suppose the RAZR was on the head designer’s table at the time when he was sketching out Nokia N76 – a metal keypad is here, along with dents at the bottom and other bits and pieces giving away its origin.
As a matter of fact, the company has managed to squeeze the hardware of the N76 into a casing only 13.7 mm deep, not due to cutting-edge alterations to the chassis; basically they have made it taller. Generally speaking Nokia 6290 is an exact replica of Nokia N76 – there aren’t many differences to dwell upon. While the 6290 measures 94x50x20.8 mm, the N76 presents us with 106.5x52x13.7 mm, meaning that it is a tad wider, almost 1 cm taller and all this for being reasonably thin.
Since we have started comparing these two handsets, then another place where the N76 falls short of Nokia 6290 is battery life. Nokia N76 utilizes a 700 mAh battery (BL-4B); as the manufacturer claims it can keep the phone up and running for up to 200 hours in standby mode and provides about 2 hours 45 minutes of talk time. A curious fact – for Nokia 6290 carrying a 950 mAh BL-5F onboard, the maker says 240 hours of lifetime in standby mode is its utmost limit. Keeping in mind that it would be a hastiness to take for granted what manufacturer claims regarding battery life, let us try to look into the real battery life put up by Nokia N76, or, better to say, how much worse it will be. Examining capacity of two batteries point-blank, then the gap will make up 35 percent, at that in normal conditions on average load Nokia 6290 manages to keep itself alive for about 2 days. Taking account of nonlinearity of charge wearing out, we can rightfully state that Nokia N76 is a handset that will require you to plug in the charge every evening, of course, if you are actually going to use it.
Software-wise these two models are wholly identical, the only difference is possibility to go into landscape mode on the internal display. Support for A2DP profile is currently missing.
Apart from the battery life and absence of stereo-speakers, Nokia 6290 and Nokia N76 are twins. I should mention it that the design of the senior solution is different and one could hardly make a mistake about that – Nokia N76 is positioned as a fashion solution, with vivid trims speaking in favor of this assumption, specifically red and black color schemes. Overall the handset looks pretty stylish and will surely appeal to many; to me this is what the company is betting on – to draw attention of those who have struck Nokia 6290 off their short-lists for some reasons.
Google piracy
Google has really done a great job. Imagine a futurewhere there won't be any software available on your pc. Your OS won'tallow you to install anything because of compatibility issues. hehe.or it is also possible that there won't be any OS at all. You will just have firefox installed on your computer. You login using your Google id in your SAS account. It will ask you what software you want to start and you choose... let's say MS .net, high system configuration will not be needed. All you need is high speed internet connection.Started enjoying it? Think Again Just imagine how 'dangerous' it can be forpirates like us. hehe. You have to buy user license for it and NO, you won'tbe able to share it with your frnd. You won't be able to crack it becauseapplication will not be available on your system, only frontend willbe accessible. The big daddy of hackers may be able to hack into google serverand create a free account, but as far as novices like us are concerned they have to fish out their money. So no privacy OOPS! piracy at all. Since applications willbe used in realtime, so the number of logons will be available to theprovider and it will be able to deny access to your friend who'strying to use the same user id.NO PIRACY MEANS NO PIRACY.No one will Trust you. You want to play music? Then buy it and hear it online.That will be so cool, huh!. Everything that you do with your PC will be monitored and moderated. We will have a "crime free" world where you can't even see your faviorite movie on your PC if you didn't buy it. So should we support SAS?Hey one more thing, The motto of Google is don't be evil. I hope they are not preaching this to us. What if they start forcing it on us. Scared??? If Microsoft is The Satan of technolgy then If Google is the christ of technology? Who wants a goodie- goodie sort of thing. We all just want to be human. Isn't it.
Subscribe to:
Posts (Atom)




























